Fox News Flash top headlines for December 3
Fox News Flash top headlines are here. Check out what's clicking on Foxnews.com.
If you’ve ever wondered where your stolen credit card turns up, a cybersecurity firm is offering hard proof.
Your credit card data is typically stolen in two ways. One is after a data breach like the Capital One incident that affected 106 million customers. The other is e-skimming, where hackers inject JavaScript code into website payment processing pages in order to pilfer credit cards and account data from customers.
During the holiday season, cybercriminals turn to e-skimming, Greg Foss, Senior Cybersecurity Strategist at VMware Carbon Black, told Fox News.
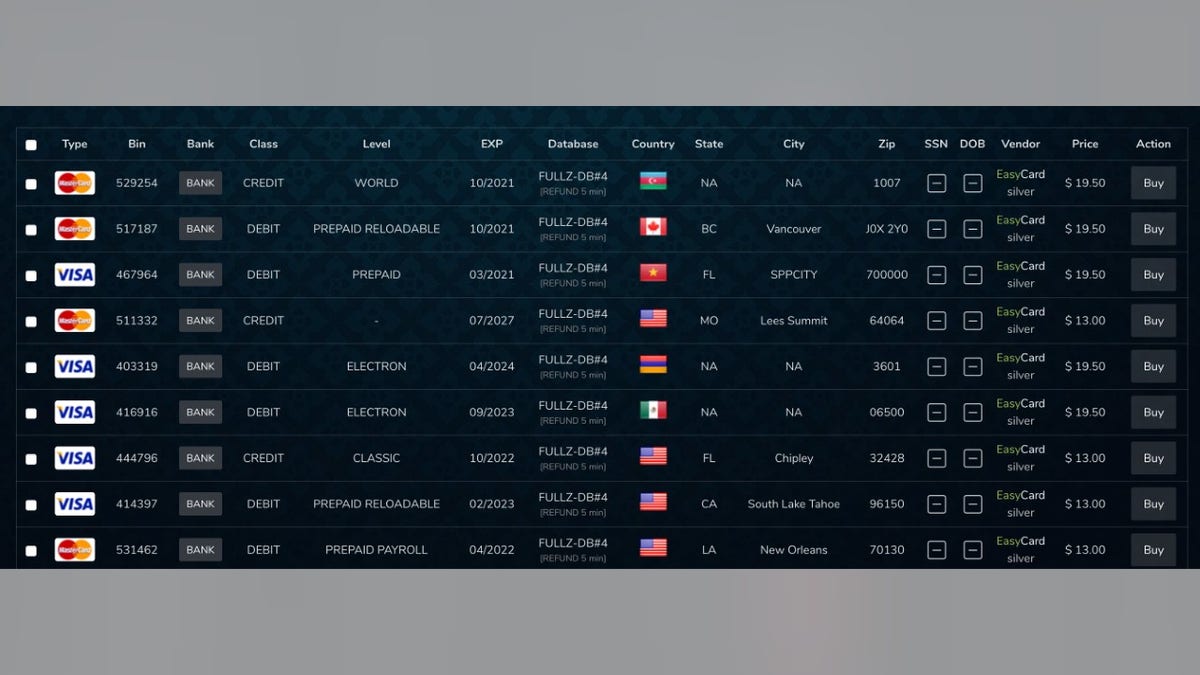
A screenshot from the Russian Market, a forum that specializes in carding and related services. (Credit: VMware Carbon Black)
FBI WARNS OF NEW CORONAVIRUS EMAIL AUTO-FORWARDING SCAM
“Magecart is one of the most prominent [criminal] groups behind this activity [to] siphon off sensitive card data,” Foss said.
Recently, Magecart has been impersonating legitimate payment applications using homoglyph attacks – for instance, creating a website “g00gle.com” instead of google.com – which fools victims into visiting the malicious site, Foss explained.
The endgame for cybercriminals is peddling stolen credit cards that go for an average rate of $10 to $20 per card on the dark web, according to Foss. PayPal accounts sell for $2 to $10 per account, with accounts holding more money costing even more.
The stolen credit card data is typically offered in a shopping cart format, where the “buyer” can check off which credit cards they want to purchase based on a menu of available credentials.
Those credentials often include Social Security numbers and the date of birth. “While there are other services that specialize in the aggregation and resale of [social security number and date of birth] data, many carding forums also provide this information in conjunction with credit cards,” Foss said.
“This information makes the credit cards all that more valuable and extends the use-cases for this data exponentially,” he added.
Perhaps not surprisingly, there's a lot of this pilfered data on the dark web.
In 2019, cybercriminals sold more than 30 million credit card records on the dark web, linked to a data breach at a U.S gas station and convenience store chain.
RANSOMWARE GANG IS RAKING IN TENS OF MILLIONS OF DOLLARS
That breach, caused by an attack that compromised PoS (point-of-sale) devices, went undetected for 9 months. The breach affected 860 convenience stores – 600 of those were also gas stations.
Another ominous trend in credit card theft is ransomware. Criminals in these cases will attempt to secure the ransom payment after data has already been stolen and put up for sale on the dark web, according to Foss.
“We’ve seen these methods employed in the final stages of an attack as a means of covering the criminal's tracks and maximizing profitability,” Foss said.









































