'CyberGuy': Protecting yourself from Microsoft tech support scams
Tech expert Kurt Knutsson says scammers exploit fears, falsely claim computer issues to access your personal data.
Tech support scammers are modern-day con artists, preying on our deepest technological fears and vulnerabilities. Tammy of Flagler Beach, Florida, recently reached out to us with a concerning email:
"I think we may have been hacked by Microsoft Windows…we turned off computer after calling the Microsoft number blaring at us telling us to not touch the computer. What do we do???"
We’re sorry to hear that you’re experiencing this issue. Tammy's experience is a classic example of a prevalent tech support scam that has been targeting unsuspecting users. It’s important to note that Microsoft will never proactively reach out to you to provide unsolicited PC or technical support. These criminals have evolved their tactics to easily convince you that your computer has a critical problem needing immediate attention.
Any communication they have with you must be initiated by you. If you receive a phone call or pop-up window from someone claiming to be from Microsoft, and they tell you that your computer has a problem or has been hacked, it’s likely a scam.
GET SECURITY ALERTS, EXPERT TIPS - SIGN UP FOR KURT’S NEWSLETTER - THE CYBERGUY REPORT HERE
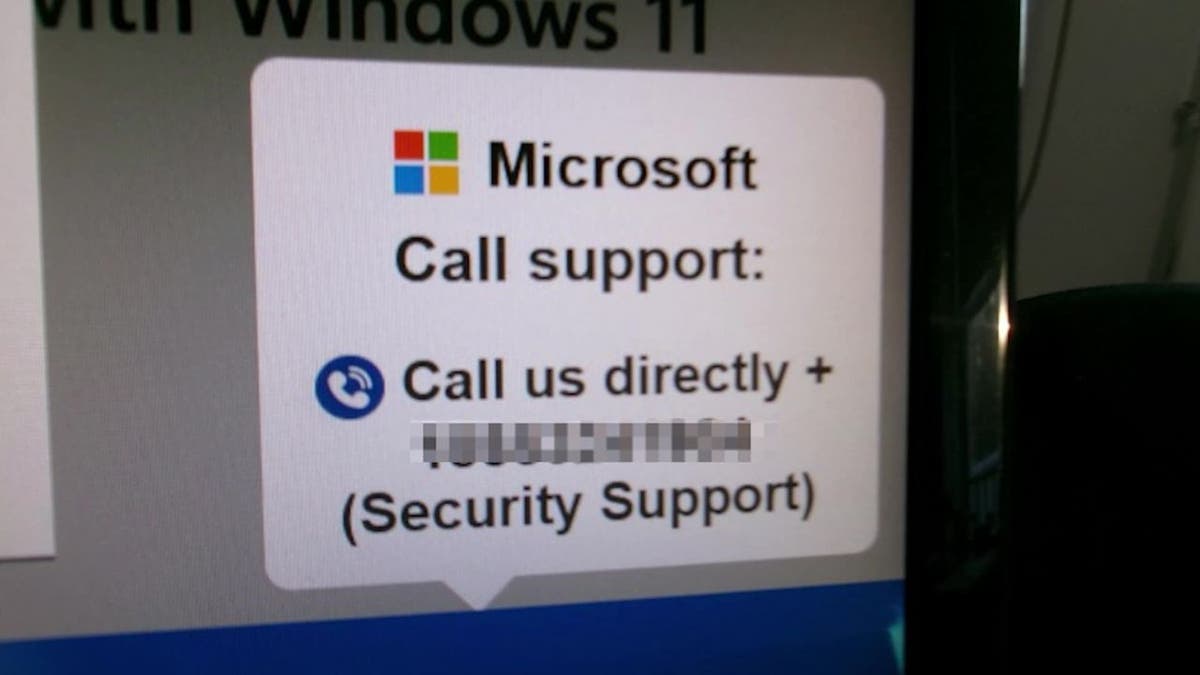
Fake Microsoft support scam pop-up (Kurt "CyberGuy" Knutsson)
Red flags scammers use to trick you into believing your computer is compromised
Tech support scammers have become master manipulators, using psychological tactics to exploit your fears and vulnerabilities. Here are the six most common warning signs that you're being targeted by a sophisticated tech support scam:
Unsolicited contact: Be wary of unexpected calls, emails or pop-ups claiming your device is compromised.
Urgency and scare tactics: Scammers often create a sense of panic, claiming hackers could access your devices and data imminently.
Requests for remote access: A major red flag is if someone you didn't contact asks to remotely access your computer.
Pressure for immediate payment: Be suspicious of demands for payment, especially via non-reversible methods like gift cards, wire transfers or cryptocurrency.
Impersonation of reputable companies: Scammers may claim to be from well-known tech companies like Microsoft or Apple.
Suspicious pop-up messages: Be cautious of pop-up warnings about viruses or system issues, especially those with countdown timers.
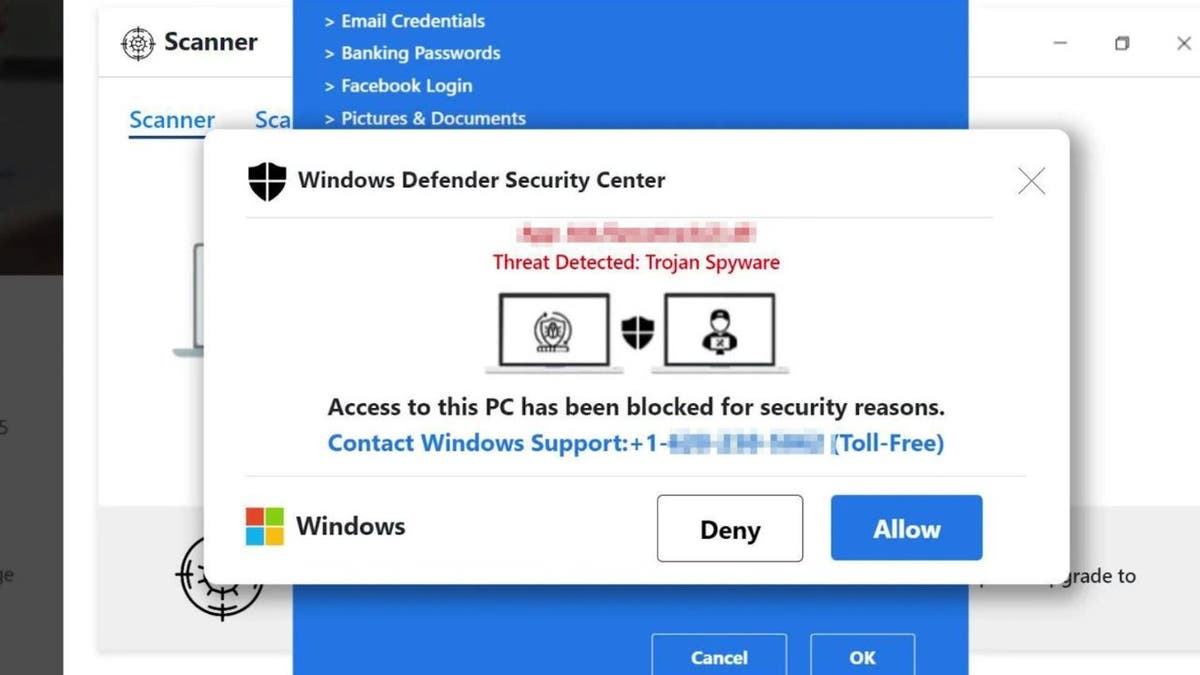
Fake Microsoft Windows scam pop-up (Kurt "CyberGuy" Knutsson)
9 WAYS SCAMMERS CAN USE YOUR PHONE NUMBER TO TRY TO TRICK YOU
Immediate steps to take if you are targeted
To quickly secure your information and minimize potential damage, follow these steps.
1) Disengage immediately: Hang up the phone or close any suspicious pop-ups.
2) Disconnect from the internet: This can prevent potential remote access by scammers.
3) Do not provide remote access: Never give control of your device to unsolicited callers.
4) Run a security scan using strong antivirus software: Use reputable, up-to-date, strong antivirus software to check your system. The best way to safeguard yourself from malicious links that install malware, potentially accessing your private information, is to have antivirus software installed on all your devices. This protection can also alert you to phishing emails and ransomware scams, keeping your personal information and digital assets safe. Get my picks for the best 2024 antivirus protection winners for your Windows, Mac, Android and iOS devices.
5) Change critical passwords: Update passwords for important accounts, especially if you've shared any information. Make sure to create strong, unique passwords. Consider using a password manager to generate and store complex passwords.
6) Enable two-factor authentication: Where possible, enable multifactor authentication. This adds an extra layer of security to your accounts.
7) Monitor your accounts: Keep an eye on your financial accounts, email accounts and social media for any unusual activity. If you think scammers have stolen your identity, consider identity theft protection here.
Identity theft companies can monitor personal information like your Social Security number, phone number and email address and alert you if it is being sold on the dark web or being used to open an account. They can also assist you in freezing your bank and credit card accounts to prevent further unauthorized use by criminals.
One of the best parts of using some services is that they might include identity theft insurance of up to $1 million to cover losses and legal fees and a white-glove fraud resolution team where a U.S.-based case manager helps you recover any losses. See my tips and best picks on how to protect yourself from identity theft.
8) Invest in personal data removal services: Using a data removal service can be an effective additional step to protect your personal information after a potential tech support scam. These services locate and remove your personal information from various online platforms, databases and data brokers. By eliminating unnecessary or outdated information, data removal services minimize your online presence, making it harder for scammers to find and exploit your data.
While no service promises to remove all your data from the internet, having a removal service is great if you want to constantly monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check out my top picks for data removal services here.
9) Contact professionals: If you’re unsure about any steps or if the situation seems severe, consider reaching out to a professional IT service.
10) Report the incident: Report the scam to your local authorities and the Federal Trade Commission in the U.S. You can also report the scam to Microsoft directly.
Remember, it’s important to stay calm and take one step at a time.

Hacker at work (Kurt "CyberGuy" Knutsson)
SPOTIFY PLAYLISTS ARE BEING HIJACKED TO PROMOTE PIRATED SOFTWARE AND SCAMS
Kurt's key takeaways
Tech support scams are designed to exploit fear and technical uncertainty. Remember that legitimate tech companies will never proactively contact you about computer issues. Always verify support through official channels, and when in doubt, consult with a trusted tech-savvy friend or professional.
Have you or someone you know ever been targeted by a tech support scam? Share your experiences and how you dealt with it by writing to us at Cyberguy.com/Contact.
For more of my tech tips and security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you'd like us to cover.
Follow Kurt on his social channels:
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the best way to stay private, secure and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data removal services?
- How do I remove my private data from the internet?
New from Kurt:
Copyright 2024 CyberGuy.com. All rights reserved.









































