Nikki Haley: Biden has to go after Russia’s energy sector, give Ukraine aid
Former U.N. Ambassador Nikki Haley on the U.S. imposing additional sanctions against Russia during their war on Ukraine.
The Federal Bureau of Investigation wrested control of thousands of routers and firewall appliances away from Russian military hackers by hijacking the very same devices Moscow's spies had been using to set up a "botnet" – a network of hacked computers that can bombard other servers with rogue traffic.
"Fortunately, we were able to disrupt this botnet before it could be used," U.S. Attorney General Merrick Garland said during a news conference.
The FBI conducted the court-authorized operation in March 2022, disrupting a two-tiered global botnet of thousands of infected network hardware devices under the control of a threat actor known as Sandworm, which the U.S. government previously attributed to the Main Intelligence Directorate of the General Staff of the Armed Forces of the Russian Federation (the GRU), the Justice Department announced in a statement.
RUSSIA INVADES UKRAINE: LIVE UPDATES
The operation copied and removed malware from firewall devices that Sandworm used for command-and-control of the botnet. While the operation did not access the Sandworm malware on the underlying victim devices, the disabling of the command-and-control mechanism severed the bots from the Sandworm devices' control, disrupting the Russian military hacker operation.
"Through close collaboration with WatchGuard [Technologies Inc.] and our law enforcement partners, we identified, disrupted and exposed yet another example of the Russian GRU’s hacking of innocent victims in the United States and around the world," U.S. Attorney Cindy K. Chung for the Western District of Pennsylvania said in a statement.

Russian President Vladimir Putin is seen above. The country has consistently denied any role in the poisoning of an ex-spy and his daughter on U.K. soil. (Alexei Druzhinin, Sputnik, Kremlin Pool Photo via AP)
"Such activities are not only criminal but also threaten the national security of the United States and its allies," Chung added. "My office remains committed to working with our partners in the National Security Division, the FBI, foreign law enforcement agencies and the private sector to defend and maintain our nation’s cybersecurity."
"The FBI prides itself on working closely with our law enforcement and private sector partners to expose criminals who hide behind their computer and launch attacks that threaten Americans’ safety, security and confidence in our digitally connected world," Special Agent in Charge Mike Nordwall of the FBI’s Pittsburgh Field Office said in a statement. "The FBI has an unwavering commitment to combat and disrupt Russia’s efforts to gain a foothold inside U.S. and allied networks."

(Getty Images)
The malware involved, Cyclops Blink, targets network devices manufactured by WatchGuard Technologies Inc. and ASUSTek Computer Inc.
UKRAINIAN INTELLIGENCE RELEASES NAMES OF MORE THAN 600 ALLEGED RUSSIAN SPIES
While the FBI operation succeeded in copying and removing the malware from all remaining identified command-and-control devices and prevented Sandworm from accessing these devices, WatchGuard and ASUS devices that acted as bots may remain vulnerable to Sandworm if device owners do not take the WatchGuard and ASUS recommended detection and remediation steps, DOJ warned. The department urged network defenders and device owners to review the department's Feb. 23 advisory and the guidance documents that WatchGuard and ASUS released.
The operation took place nearly a month into Russia's invasion of Ukraine.

(Reuters)
Late last month, Ukrainian intelligence released a purported list of more than 600 Russian spies. Shortly before that, Russian President Vladimir Putin reportedly put two FSB agents who reportedly scouted Ukraine on house arrest after Russia's Ukraine invasion proved far more difficult than Putin appears to have considered at first.
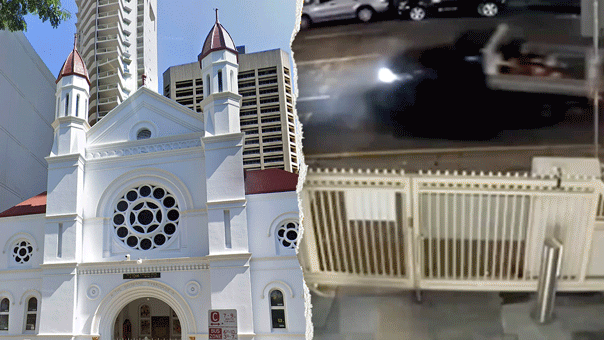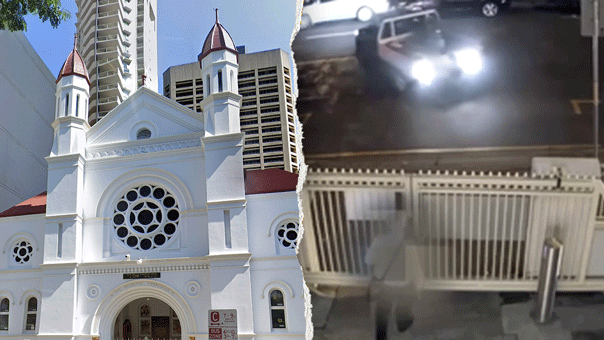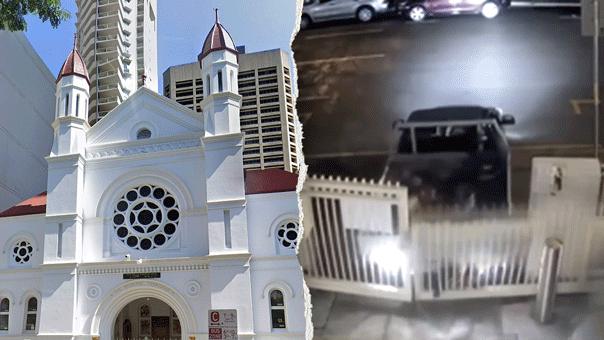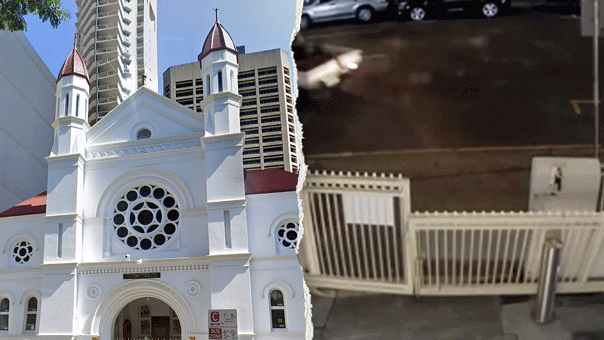
Rep. Ritchie Torres, D-N.Y., called on the FBI to investigate the Russian Diplomatic Compound, located in New York City, which experts previously told Fox News Digital houses diplomats who are in the U.S. to spy on America.

A view of the Russian Diplomatic Compound at 355 West 255th Street (Google Maps)
"We have been appalled and alarmed by Vladimir Putin's unprovoked war of aggression against Ukraine. We have been appalled by his war crimes against the Ukrainian people, and it is in that context that I have formally requested that the FBI open an investigation into reports of espionage at the Russian diplomatic compound," Torres told reporters Tuesday about the white high-rise tower located at 355 West 255th Street, in the Bronx borough.
CLICK HERE TO GET THE FOX NEWS APP
The Bronx Democrat called it "both metaphorically and literally a structure of surveillance."