Election hacking DEF CON 2019
The Fox News Investigative Unit got a first-hand look at the vulnerabilities of U.S. election equipment at the DEF CON 27 Hacking Conference in Las Vegas.
I may have the keys to open voting machines used in states across the country, and that is not a good thing.
I am not an election official. I am not a voting machine expert, operator, or otherwise affiliated with any federal, state or local government agency.
I am simply an investigative journalist who, upon learning that the types of keys used for these machines are apparently widely available for purchase on the Internet, was prudent enough to ask to take a few keys home as souvenirs from my recent trip to the DEF CON 27 Hacking Conference in Las Vegas.

Keys that open election equipment, like voting machines, are apparently available for purchase on websites like Amazon, since they utilize locks that pair with common-shape keys. Harry Hursti, organizer of the DEF CON Hacking Conference "Voting Village," had a bag of such keys on-hand to show attendees how vulnerable the locks on some voting machines can be. (Fox News)
Now, I have access to machines that have been used or are currently in-use in 35 different states. Swing-states, coastal icons and the heartland, experts say. The coolest and probably most disturbing SWAG ever, hands-down.
VOTING MACHINES CAN BE HACKED IN TWO MINUTES, EXPERT WARNS
“These are the keys to the kingdom,” explains Harri Hursti, a hacker and data security expert with Nordic Innovation Labs. Hursti, who helped organize the DEF CON “Voting Village,” was speaking both literally and metaphorically, since some of these keys actually open the memory card enclosure on certain machines.
The problem, Hursti says, is that many of the locks used for these machines work with basic keys that can be easily replaced over time, or in the event they are lost. Some of the keys are so universal that they not only open voting machines, but also mini-bars and even some elevators.
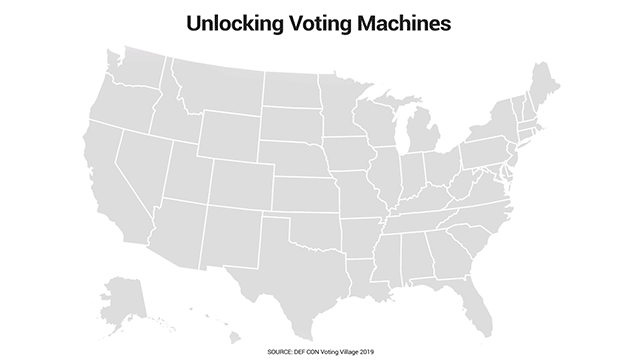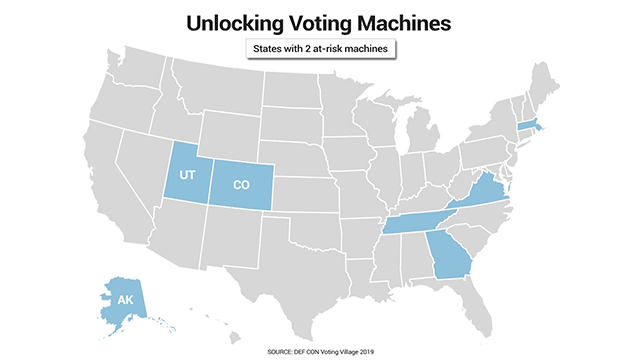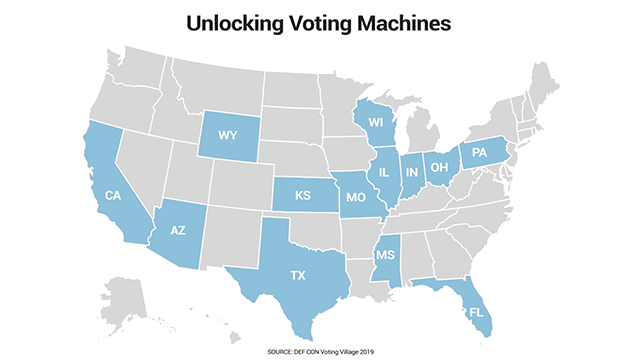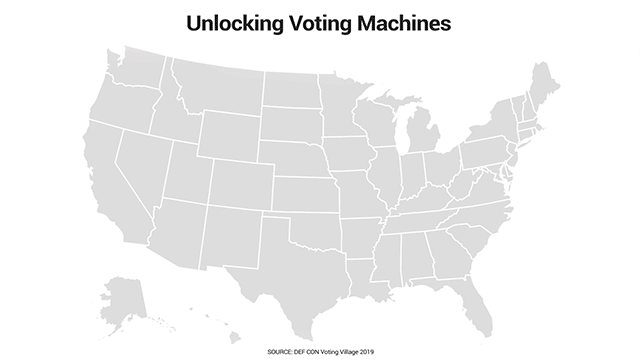
Fox News obtained keys at the DEF CON 27 Hacking Conference that are widely available for purchase, and that apparently open various types of U.S. election equipment past and present. The above animation shows the states where the keys Fox was given can apparently open such machines. (Data Source: DEF CON Voting Village 2019)
Ordering what is effectively a skeleton key off of Amazon is not the kind of “hacking” you might think of at a place like DEF CON’s Voting Village, or when brainstorming the possible vulnerabilities of the supposedly secure equipment used in U.S. elections in general. But here we are.
Indeed, the types of keys I was shown at the DEF CON “Voting Village” are available on sites like Amazon, eBay and others, as Hursti suggested.
FOREIGN HACKERS HAVE US ELECTION NETWORKS IN THEIR CROSSHAIRS, REPORT SAYS
“This [machine] is used in 18 different states, many different swing-states. You can disrupt the ballot, you can make it say something it’s not supposed to say. And that’s undermining our democracy.”
Sure, I learned about plenty of other digital backdoors and other disturbing vulnerabilities concerning U.S. election equipment at DEF CON. Like the “hidden feature” that Hursti says was only recently discovered in a machine that’s been in use and under the microscope for more than a decade.
“A hidden feature that enables you to reopen the polls silently, and insert more ballots and print the new evidence of the election,” Hursti says. And despite believing that the manufacturers had learned from previously exposed vulnerabilities on that machine over the years, “these [newly discovered] features had been missed” the entire time, Hursti says.
I watched Hursti explain this new discovery to Rep. Eric Swalwell, D-Calif., one of the numerous lawmakers who attended this year’s DEF CON, and whose face seemed to drop upon learning of the new revelation. That’s likely because this particular machine has been in use in his home state of California for years.
There was a team of students who rigged two different machines to play the retro classic “PONG” with each other from across the room. A different group of researchers was able to hack a piece of equipment, previously used to check-in and verify voters on Election Day, to run the eponymous video game, “DOOM.”
35 MILLION VOTER RECORDS UP FOR SALE ON THE DARK WEB, REPORT SAYS
That latter machine utilized a commonly available tablet with both forward and rear-facing cameras. A media representative for Election Systems & Software (ES&S), one of the companies behind that particular piece of equipment and others at DEF CON, said "voting machines don't have cameras. Perhaps you are referencing our previous version of e-pollbook, used to check in and verify voters."
Those tablets, they said, were only used "in certain states to speed up the voter check-in process," and that their equipment "does not photograph voters or cast ballots, and there is no way the ballot can be tied to the voter at registration."
You can decide how reassured you are by those statements if you ever find yourself staring a webcam in the face while checking-in on Election Day.
One voting machine was discovered to have a password of “1111.” Better than the voter ID machine with NO password.
And I watched as yet another voting machine was physically dismantled, memory card and all, with just fingernails and a ballpoint pen. Rachel Tobac, CEO of SocialProof Security, a company that specializes in “social engineering” and security assessments, walked me through that last process in less than 90 seconds. And this was only her second year of hacking voting machines.
In the “kids area” at DEF CON, known as the “r00tz Asylum,” children barely out of middle school had hacked a simulated campaign contributions website to reveal donations from a deep-pocket donor named “spaghetti.” Jokes aside, the power to change the names and amounts of political donations on official state websites is no laughing matter.
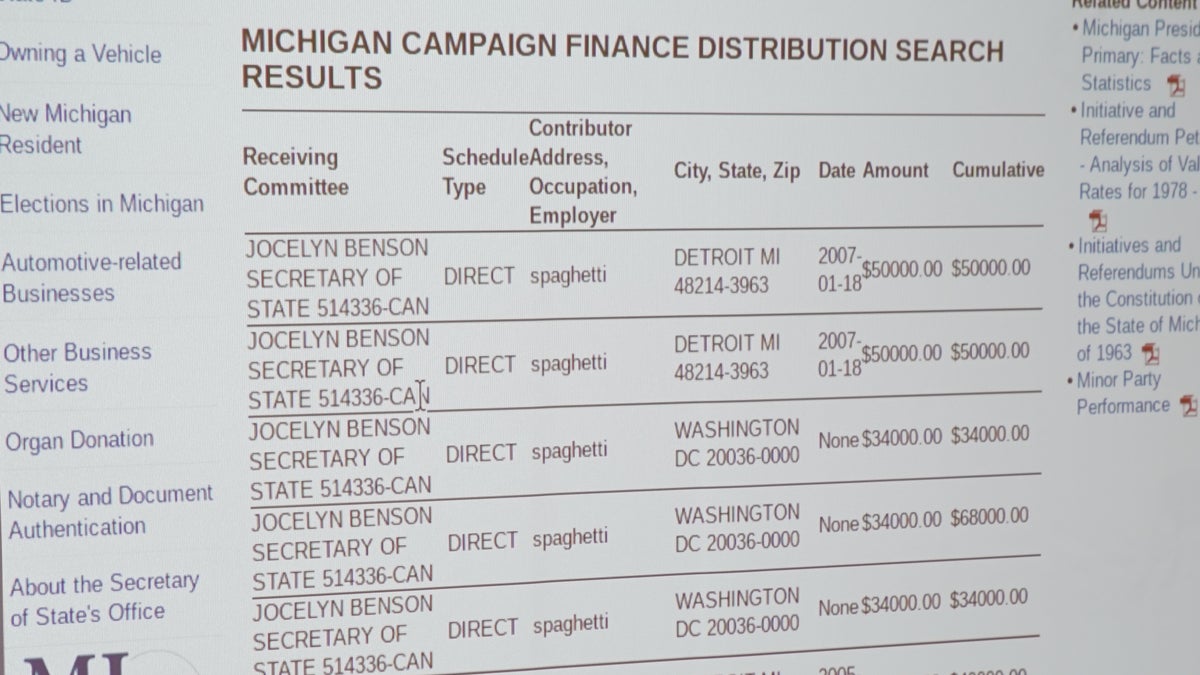
A simulated campaign contributions website is hacked by children at the DEF CON 27 Hacking Conference "r00tz Asylum" kids area in Las Vegas. The simulated website was hacked to reveal a deep-pocket donor named "spaghetti." (Fox News)
HACKERS EASILY BUST INTO VOTING MACHINES, IN CONFERENCE CHALLENGE
There were signs that some of the problems with U.S. election equipment are being addressed, like the significantly larger contingent of lawmakers at this year’s DEF CON, as well as election officials and even congressional staffers from both sides of the aisle. Or the fact that more than a dozen actual voting machines were available for tinkering at this year’s Voting Village, some of them by the manufacturers themselves.
Dominion Voting, another company that produces election equipment, "sent representatives and demo equipment to DEF CON this year in the hopes of finding more ways to work with researchers and white hat hackers," according to a representative.
One prominent member of the hacking community at DEF CON told Fox that they felt as if the Voting Village's "scorched earth" approach of dismantling voting machines in a public space may no longer be the best way to encourage a public dialogue with the companies behind the tech. That same person said it's a very good sign that there were apparently representatives from at least one such company at DEF CON this year, with gear in tow. They also admitted that having election equipment that utilizes master keys sold on the Internet seems like an obvious and easily fixable problem.
There are also technological advancements being researched to try and make the voting system more secure, like a new $10 million machine funded by the DoD, and the concept of combining blockchain technology with paper ballots – a federal elections Frankenstein that is at least three elections away from becoming a possible reality, according to people working on the project.

A piece of U.S. elections equipment is hacked at the DEF CON 27 Voting VIllage in Las Vegas to show an animated "Nyan Cat," among other things.(Fox News)
While that particular project is still a few years off, mobile blockchain voting has already gone through a trial in West Virginia, and the state apparently plans to use it again in 2020. The trial was focused mainly on allowing voters in the military overseas to cast their ballots, and state election officials have reportedly said that they felt this technology presented a more-secure alternative to ordinary Internet voting.
However, in just the last month an Australian company working on a blockchain-based voting system shut down due to unspecified legal reasons, and a researcher in France released a report detailing how he cracked Moscow's Internet voting system one month before the country's elections.
All of this being said, the experts who know better than anyone just how vulnerable these machines are say that none of these things should discourage anyone from heading to the polls.
"The security researchers who find these vulnerabilities? We’re the first people in line on election day (when we aren’t volunteering as poll workers)," Matt Blaze, another security expert with the DEF CON Voting Village, wrote in a tweet.
Regarding some of the claims emerging from this year's election hacking festivities, Dominion's representative said the company would "need to be able to review the full report from DEF CON before responding to any claims or inquiries."
On the issues of locks and keys, and whether they support the efforts that go on at a place like DEF CON, ES&S explained to Fox that the company "submits its equipment to testing by independent security researchers and proactively seeks to work with independent experts in election security," in addition to partnering with the likes of the Department of Homeland Security. They added that there are additional safeguards in place beyond the obvious locks themselves.

At the DEF CON Hacking Conference Voting Village, Fox News is shown a prototype for a research project that could combine blockchain technology and paper ballots embedded with codes that can be scanned digitally. (Fox News)
And while ES&S also suggested that there is no evidence that a vote in a U.S. election has ever been compromised by a cybersecurity breach, Tobac and countless others at DEF CON this year made it clear that time is of the essence when it comes to solving the apparent problems that remain with some of this equipment.
CLICK HERE TO GET THE FOX NEWS APP
“This [machine] is used in 18 different states, many different swing-states,” Tobac says. “You can disrupt the ballot, you can make it say something it’s not supposed to say. And that’s undermining our democracy,” she added.
Plenty more coverage to come from my inaugural trip to DEF CON. Got a tip for me, DEF CON-related or otherwise? Send me a DM on Twitter, @_gonzoAD, or find me on Signal - alexdiaz36.