'CyberGuy': Don't take the bait
Kurt Knutsson provides advice on how to identify safe email links and tips for safeguarding your email account against phishing attacks.
Imagine this nightmare scenario. You receive an email from your health insurance provider, let's say it's Blue Shield, asking you to update your personal information by clicking on a link. You think it’s a routine request, so you click on the link and enter your name, date of birth, and social security number. The next thing you know, your identity is stolen, and your credit score is ruined.
This is a common occurrence of a phishing attack, a type of online scam that targets your email account. Phishing attacks are designed to trick you into clicking on malicious links, opening infected attachments, or providing personal information to hackers who want to steal your money, identity, or data. It's definitely a concern of Don, from Michigan, who wrote to us asking,
"You mention not to tap/select links in emails, how do I know if email links are OK to select? (like Blue Cross Blue Shield??)" — Don, Michigan
Well, Dan, that is a great question that we will answer and share some tips on how to protect yourself from these attacks.

A person typing on a laptop (Kurt "CyberGuy" Knutsson)
How do I know if an email link is safe to select?
Here are three simple and effective ways to check if an email link is safe to select. These tips will help you avoid clicking on links that could lead you to phishing websites or malware downloads.
1) Inspect the link
One of the best ways to check if a link is safe to select is to inspect the link before clicking on it. To do this, you can carefully hover your mouse over the link and look at the web address that appears. If the web address looks suspicious, misspelled, or unfamiliar, don’t click on it.
When in doubt, go directly to the company’s website by manually typing in the web address, or searching for the site in a search engine. Most often, the first or second result that comes up is legitimate. If you see the word "Sponsored "above the search result, take a beat before clicking it and consider clicking on the result below it.
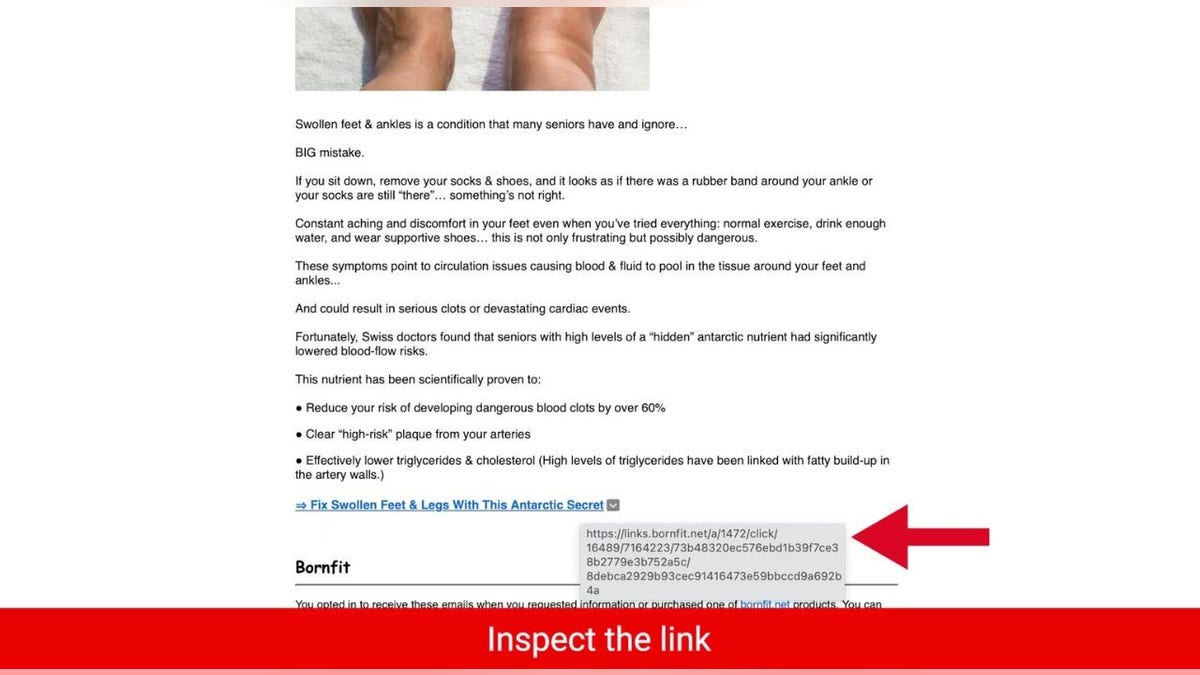
Example of inspecting a link in an email (Kurt "CyberGuy" Knutsson)
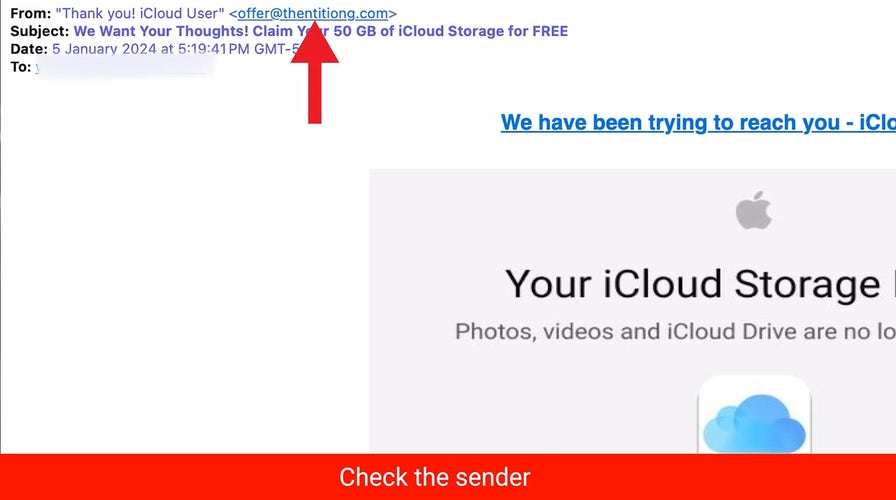
2) Verify the sender of the email
Another way to check if an email link is safe to select is to verify the sender of the email. Make sure that the email is from a legitimate source and not a spoofed or fake one. Scammers often use slight variations or impersonate legitimate sources. You can do this by looking at the sender’s email address and name. If the email address or name doesn’t match the sender’s identity, don’t trust the email.
If you’re still unsure about the authenticity of an email or a link, you can contact the sender directly and ask them to confirm. Don’t use the contact information provided in the email, but look for it on their official website or other trusted sources. Whatever you do, do not click on any links or provide personal information.
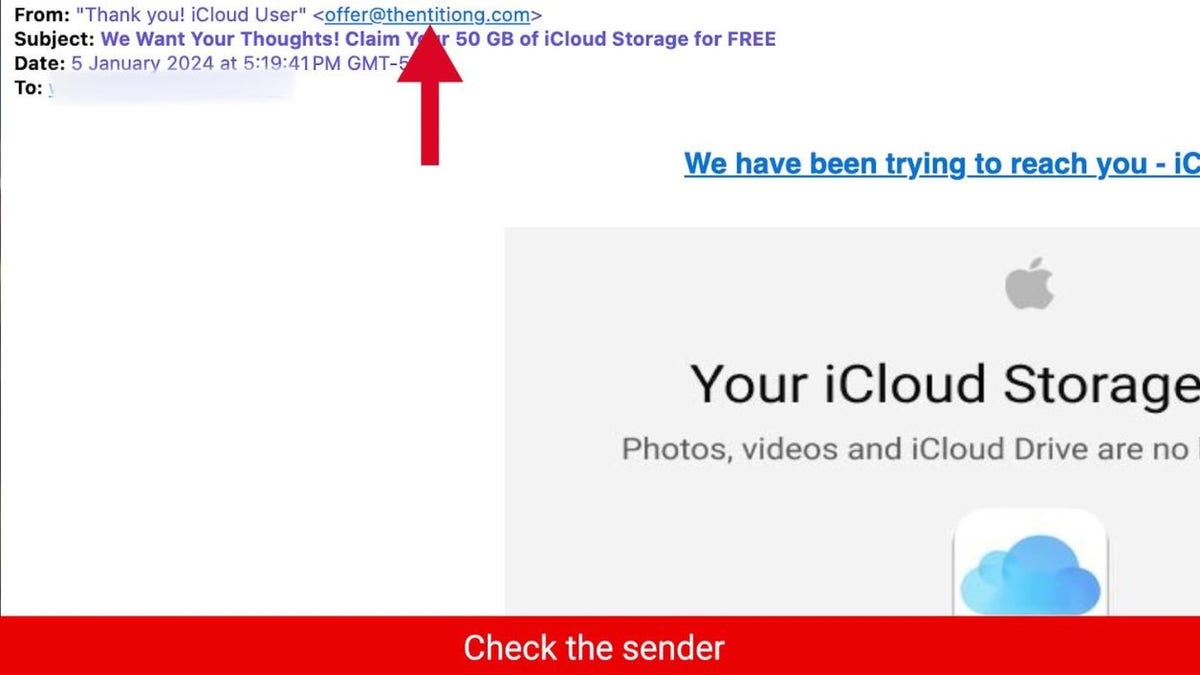
Example of how to check who an email is from (Kurt "CyberGuy" Knutsson)
MORE: HOW TO PROTECT YOUR IPHONE FROM CYBERATTACKS WITH LOCKDOWN MODE
3) Before you click on any links or email attachments, ask yourself 3 questions
Pause before clicking. Before you click on any link or open any attachment, take a moment to evaluate it and ask yourself these 3 questions:
- Do I know the sender?
- Do I trust them?
- Did I expect them to send me a link or an attachment?
If the answer is no to any of these questions, then you should absolutely not click on any link or open the attachment. These links or attachments may look harmless, but they can actually contain harmful malware that can damage your device or steal your data. It’s better to be safe than sorry when it comes to email attachments.

Person typing on a smartphone (Kurt "CyberGuy" Knutsson)
MORE: ANOTHER HOME THERMOSTAT FOUND VULNERABLE TO ATTACK
How to secure your email account from phishing attacks
Here are 6 tips to protect your email account from phishing attacks.
#1 CyberGuy tip: Use antivirus software: This is perhaps one of the best investments you can make for yourself to protect yourself from phishing scams. Having antivirus software actively running on your devices will make sure you are stopped from clicking on any malicious links or from downloading any files that will release malware into your device and potentially have your private information stolen. Read my review of my best antivirus picks here.
2) Enable two-factor authentication (2FA): Whenever possible, enable 2FA for your online accounts. This adds an extra layer of security by requiring a second form of verification, such as a unique code sent to your phone, in addition to your password.
3) Keep software up to date: Regularly update your operating system, web browsers, and antivirus software to ensure they are equipped to detect and prevent the latest threats. You can regularly check for these updates on your device's settings app for software updates, and you can go to your App Store or Google Play Store (depending on the device you have) to check for updates on individual apps. Follow these steps here.
4) Be cautious with personal information: Be wary of sharing sensitive information online, especially if it's unsolicited or seems suspicious. Legitimate organizations rarely ask for personal details via email.
5) Report suspicious emails: If you receive a suspicious email claiming to be from a specific organization, report it to that organization's official support or security team so they can take appropriate action.
6) Educate yourself and others: Stay informed about the latest phishing tactics and share this knowledge with friends, family, and colleagues. Awareness is a powerful tool in preventing scams.
MORE: FACEBOOK ACCOUNTS HIT WITH MALICIOUS AD ATTACK WITH DANGEROUS MALWARE
What should you do if you've clicked a link and installed malware on your device?
If you've been hacked, it's not too late. There are several ways you can protect yourself from hackers, even when they have access to your information.
Scan your device for malware
First, you'll want to scan your computer with a reputable and legitimate antivirus program. See my expert review of the best antivirus protection for your Windows, Mac, Android & iOS devices.
Change your passwords immediately
If you've inadvertently given your information to hackers or malicious actors, they could have access to your social media or banking accounts. To prevent this, you should change your passwords for all your important accounts as soon as possible. However, you should not do this on your infected device, because the hacker might see your new passwords. Instead, you should use ANOTHER DEVICE, such as your laptop or desktop, to change your passwords. Make sure you use strong and unique passwords that are difficult to guess or break. You can also use a password manager to generate and store your passwords securely.
Monitor your accounts and transactions
You should check your online accounts and transactions regularly for suspicious or unauthorized activity. If you notice anything unusual, report it to the service provider or the authorities as soon as possible. You should also review your credit reports and scores to see signs of identity theft or fraud.
Use identity theft protection
Phishing emails target your personal information. Hackers can use this information to create fake accounts in your name, access your existing accounts, and pretend to be you online. This can cause serious damage to your identity and credit score.
To avoid this, you should use identity theft protection services. These services can track your personal information, such as your home title, Social Security Number, phone number, and email address, and notify you if they detect any suspicious activity. They can also help you freeze your bank and credit card accounts to stop hackers from using them. Read more of my review of best identity theft protection services here.
Contact your bank and credit card companies
If hackers have obtained your bank or credit card information, they could use it to make purchases or withdrawals without your consent. You should contact your bank and credit card companies and inform them of the situation. They can help you freeze or cancel your cards, dispute any fraudulent charges, and issue new cards for you.
Alert your contacts
If hackers have accessed your email or social media accounts, they could use them to send spam or phishing messages to your contacts. They could also impersonate you and ask for money or personal information. You should alert your contacts and warn them not to open or respond to any messages from you that seem suspicious or unusual.
Restore your device to factory settings
If you want to make sure that your device is completely free of any malware or spyware, you can restore it to factory settings. This will erase all your data and settings and reinstall the original version. You should back up your important data before doing this, and only restore it from a trusted source.
MORE: HOW HACKERS ARE TARGETING X VERIFICATION ACCOUNTS TO TRICK YOU
Kurt's key takeaways
Making you and your family resilient from these growing dangers needs to be your number one priority. Protecting yourself from phishing attacks is crucial. Falling victim to such scams can result in identity theft, financial losses, and data breaches. Don't let yourself become a target. By following the steps we’ve outlined above and staying vigilant, you can significantly reduce the risk of falling prey to phishing attacks. Your online security is in your hands, so make informed choices to protect your personal information and data.
Have you ever encountered a suspicious email or phishing attempt? How did you handle it, and what did you learn from the experience? Let us know by writing us at Cyberguy.com/Contact.
For more of my tech tips & security alerts, subscribe to my free CyberGuy Report Newsletter by heading to Cyberguy.com/Newsletter.
Ask Kurt a question or let us know what stories you'd like us to cover.
Answers to the most asked CyberGuy questions:
- What is the best way to protect your Mac, Windows, iPhone and Android devices from getting hacked?
- What is the best way to stay private, secure and anonymous while browsing the web?
- How can I get rid of robocalls with apps and data-removal services?
Copyright 2024 CyberGuy.com. All rights reserved.