WHO official praises China for response to coronavirus
Why is the ruling class still sucking up to China? Reaction from Dave Rubin, host of 'The Rubin Report.'
Get all the latest news on coronavirus and more delivered daily to your inbox. Sign up here.
EXCLUSIVE: Since the coronavirus pandemic began sweeping across the globe, the World Health Organization (WHO) has become the target of an array of cybersecurity attacks – but recent efforts to hack into the system have some cybersecurity experts especially concerned.
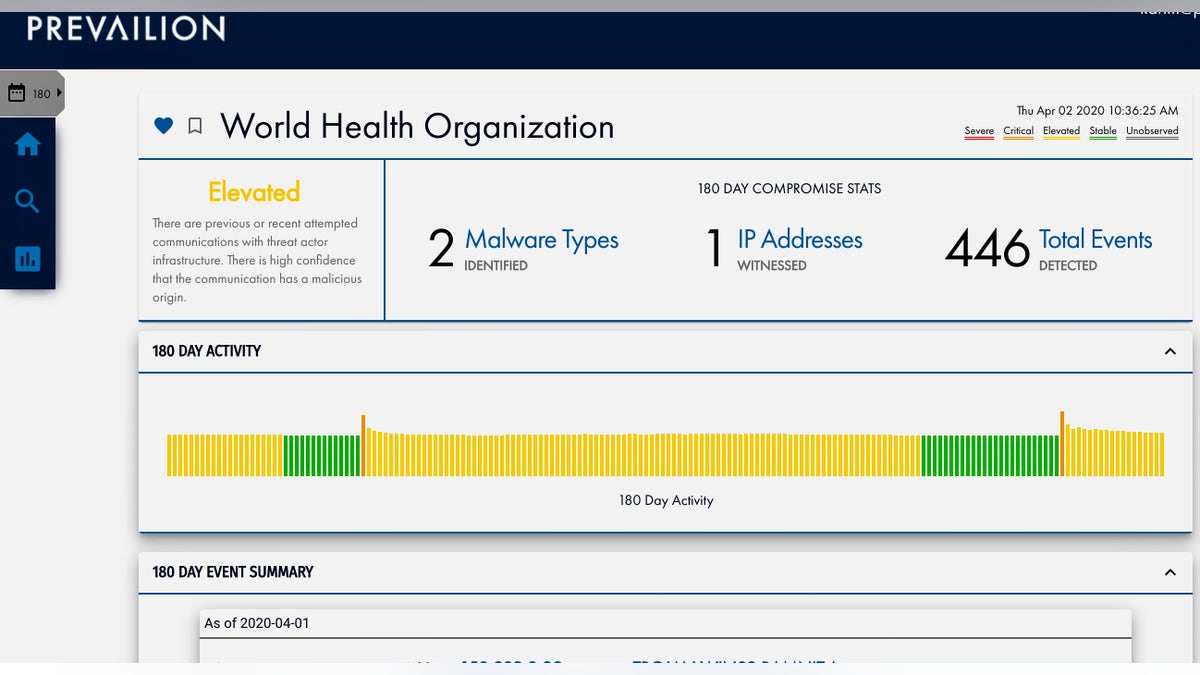
According to an investigation by U.S.-based cybersecurity firm Prevailion and shared exclusively with Fox News, the WHO has been targeted not once last month, but twice. The attacks were seemingly victorious, the analysts at the firm – which collects intel directly from malicious servers – claim and are continuing to infiltrate and exfiltrate data in vast amounts unchecked.
"WHO has been successfully breached twice recently, including a Trojan infection last month," Karim Hijazi, CEO of Prevailion, told Fox News on Friday, stressing that the hacking methods used were almost a decade old and indicated 'security negligence.' "Once something has taken hold, it has now been able to stay there. This is very concerning because all the information from countries can be stolen. The scope of this could be dramatic."
CORONAVIRUS CRIMINALS: AUTHORITIES WAGE WAR AGAINST VIRUS SCAMMERS, THIEVES, IMPOSTORS AND IDIOTS
From his lens, these apertures – which were not previously disclosed publicly – raise serious red flags that WHO is continuing to be infiltrated and exfiltrated "by adversaries."

(REUTERS/Kacper Pempel/Files)
Prevailion data showed that last month, a Ramnit Trojan infection was detected in WHO's network. It was observed "beaconing" – or calling back to the command and control server run by the hackers – over 400 times, and the infection was active over a 10-day period.
"What is concerning about this is that Ramnit is an older Trojan, so these attacks should be prevented. Ramnit was designed to steal credentials such as usernames, passwords, etc. which could have impacted WHO personnel," Hijazi explained. "And the malware writes itself to the master boot record [MBR], which means it can reinstall itself after the machine has been wiped and apparently secured."
He underscored that what this means is that WHO is porous enough to be infiltrated and exfiltrated, and there is continued communication from that malware on the inside to the open web. And that from this Trojan, pretty much anything else can be deployed, in his words, "it is a door opener for anything else to happen or be stolen."
CLICK HERE FOR COMPLETE CORONAVIRUS COVERAGE
Analytics revealed that on March 14, some 71 Trojan communications – or beacons – from inside WHO's network were bounced outside, which could indicate that either material was seized or that the malicious activity was looking for updates of itself. Then it went dark until March 17 when 139 beacons were detected from the inside to the outside.
"It's like a little spy that lives within an organization; it can steal something or request help or can ask for its friends to come to the party. It's how things like ransomware get deployed, and it can't be taken lightly. It is meant to open the door for other things to be deployed," Hijazi surmised. "This is an organization the world is leaning on, and its security should be tighter than a drum. Something this old should not be out there communicating."
The last detection was on March 24, in which three beacons were either sending something out or requesting something in.
"The fact that we're seeing something as old as Ramnit show up in WHO's network is a really bad sign. This trojan's activity that we've been tracking as it beacons back to the attacker's network is just the smoke of what is probably a much bigger fire going on inside their network," Hijazi said. "It could be a raging inferno on the inside. If something as ancient as Ramnit can get through their defenses, they have much bigger problems. It means newer malware probably doesn't have much trouble slipping in too."
Prevailion's cyberintelligence also highlighted that WHO was also breached back on Nov. 9 by the notorious Magecart malware. This is a type of malware that is best known as a digital card skimmer, but in actuality, it is just a form-grabbing malware that can capture any data entered into an online form — such as logins, an organization filling out a WHO information request or online document, registration forms, order forms, information sharing, you name it.
"This type of infection within the WHO network could be used to hack other organizations who visit the site — or any partners/registrants who are using the site to fill out forms and submit information or make requests," Hijazi continued. "We wait until malware tries to come back out to command and control, that's when we could see it. We wouldn't even know it existed unless something is beaconed out, our perspective is the adversary side."
WORLD HEALTH ORGANIZATION UNDER THE MICROSCOPE: WHAT WENT WRONG WITH CORONAVIRUS?
Hijazi pointed out that in terms of this months-old "form jacker," the "effects of that one yet to be determined" and that they have not detected any activity from this since its initial break-in.

Medical staff install patients infected with the COVID-19 virus in a train at the Gare d'Austerlitz train station Wednesday April 1, 2020 in Paris. France is evacuating 36 patients infected with the coronavirus from the Paris region onboard two medicalized high-speed TGV trains. The patients, all treated in intensive care units (ICU), are being transferred to several hospitals in Britany, as western France is less impacted by the epidemic. The new coronavirus causes mild or moderate symptoms for most people, but for some, especially older adults and people with existing health problems, it can cause more severe illness or death. (Thomas Samson, Pool via AP)
"Something like this typically gets deployed, it gets instructions and then goes outbound. It beaconed out on that date. It can lie dormant and then be deployed," he said.
Furthermore, Hijazi and his team also observed a "phishing email that comes from a legitimate WHO domain, as opposed to a fake/imitated WHO domain." This could potentially mean that hackers have gotten access to infrastructure that could send emails from WHO that won't be captured by anti-phishing technology, which identifies when something doesn't look real.
"This is going to be real because it is from a legitimate account, and it's going to be up to the receiver to make a judgment as to whether to click on the links," Hijazi highlighted, cautioning all email user to thus "proceed with caution."
Hijazi and his team also observed a “phishing email that comes from a legitimate WHO domain, as opposed to a fake/imitated WHO domain.” This could potentially mean that hackers have gotten access to infrastructure that could send emails from WHO that won’t be captured by anti-phishing technology, which identifies when something doesn’t look real. (Prevailion exclusive to Fox News)
WHO did not immediately respond to a request for comment.
Ever since the novel coronavirus, also known as COVID-19, started ravaging the globe earlier this year, WHO has been the target of endless attempted cybersecurity attacks, both as a target of attack and as an entity, they can spoof to launch countless phishing attacks on other companies and organizations.
The UN-governed health organization acknowledged this week that there had been attempts to crack into the personal email accounts of at least two staff members, they have stated they do not know who was behind the malicious messages intended to mimic Google web services and subsequently steal passwords.
A report released by Reuters on Thursday indicated that at least one attempted breach was the work of infiltrators "working in the interests of the Iranian government." The hackers endeavored to break into the personal email accounts of staff at the World Health Organization. Iran is one of the world's most infected countries and has been accused of covering up the number of cases and deaths, in addition to rampant mismanagement of the pandemic since it took root earlier this year.
Hijazi said he could not confirm the identities behind the onslaught of cyber barrages, but given the volume, indicated that there is likely a number of different criminal groups – some working independently and others working under the guise of a foreign government – attempting to break-in.
"There is no clear attribution on the attacks yet, but there is a lot of motivation across the board for different bodies to break in," he added. "We can see a specific toolset; they are from adversaries of some kind."









































