What State Dept. guidelines did Hillary Clinton violate?
Shannen Coffin: What Clinton did was illegal
Stirred by the controversy surrounding Hillary Clinton’s use of a private email server when she was secretary of state, a determined band of hackers, IT bloggers, and systems analysts have trained their specialized talents and state-of-the-art software on clintonemail.com, the domain under which Clinton established multiple private email accounts, and uncovered serious lapses in security, according to data shared with Fox News.
The findings call into question Clinton’s confident declaration, at a hastily arranged news conference in New York on Tuesday, that “there were no security breaches” in her use of a private server. One prominent figure in the hacker community, bolstered by long experience in the U.S. intelligence community, has undertaken to build a virtual “replica” of Clinton’s server configuration in a cyberlab, and has begun testing it with tools designed to probe security defenses. This individual has shared details of the Clinton system not disclosed publicly but legally obtainable.
Among other things, outside experts have managed to trace the most recent location of Clinton’s server – something she did not specify during her news conference and a subject of much speculation, as the server’s physical placement would provide early clues about whether the data stored on it was adequately secured against compromise by private-sector hackers and foreign intelligence services.
Fox News has previously reported that, with the aid of software named Maltego, experts had established that the server is up and running, receiving connectivity to the Internet through an Atlanta-based firm called Internap Network Services Corporation. Clinton’s stern insistence at her news conference that her server “will remain private” would appear to rest, then, at least in part, on the inviolability of Internap.
Now, working with publicly available tools that map network connectivity, experts have established that the last “hop” before the mail server’s Internet Protocol, or IP, address (listed as 64.94.172.146) is Internap’s aggregator in Manhattan (listed as 216.52.95.10).
“This is a very strong indication that the clintonemail.com server is in Manhattan,” the source told Fox News.
By entering the IP address for the Internap aggregator into existing databases, the experts obtained the exact geolocation coordinates for the aggregator – revealed to be on lower Broadway, at the intersection with Chambers Street, some two blocks north of City Hall. This in turn suggests that the Clinton server itself lies within close proximity – most likely former President Clinton’s Harlem office, and not as far away as the Clintons’ home in Chappaqua, N.Y.
That outside experts could so swiftly unearth such information left them convinced that the server remains, as presently configured, highly “vulnerable” to unauthorized intrusion – even if, as most observers suspect, the server, with so much publicity now attendant on it, is no longer in active use. The hackers further concluded that Clinton’s email operation was likely not much better secured when she was secretary of state.
To test that proposition, they took the relatively simple step of examining the source code on the front page of clintonemail.com. This yielded the discovery, sources told Fox News, that the Clintons have not been using the latest version of Microsoft Outlook Web Application (OWA) to send and receive emails. The most recent version of OWA is listed as 14.3.224.2, whereas tests show clintonemail.com to be using the older 14.2.390.1.
“[It’s] an indication they’re not keeping up with software upgrades,” one hacker told Fox News. “If I were a bad guy, I'd start looking for any vulnerabilities in that older version they're using.”
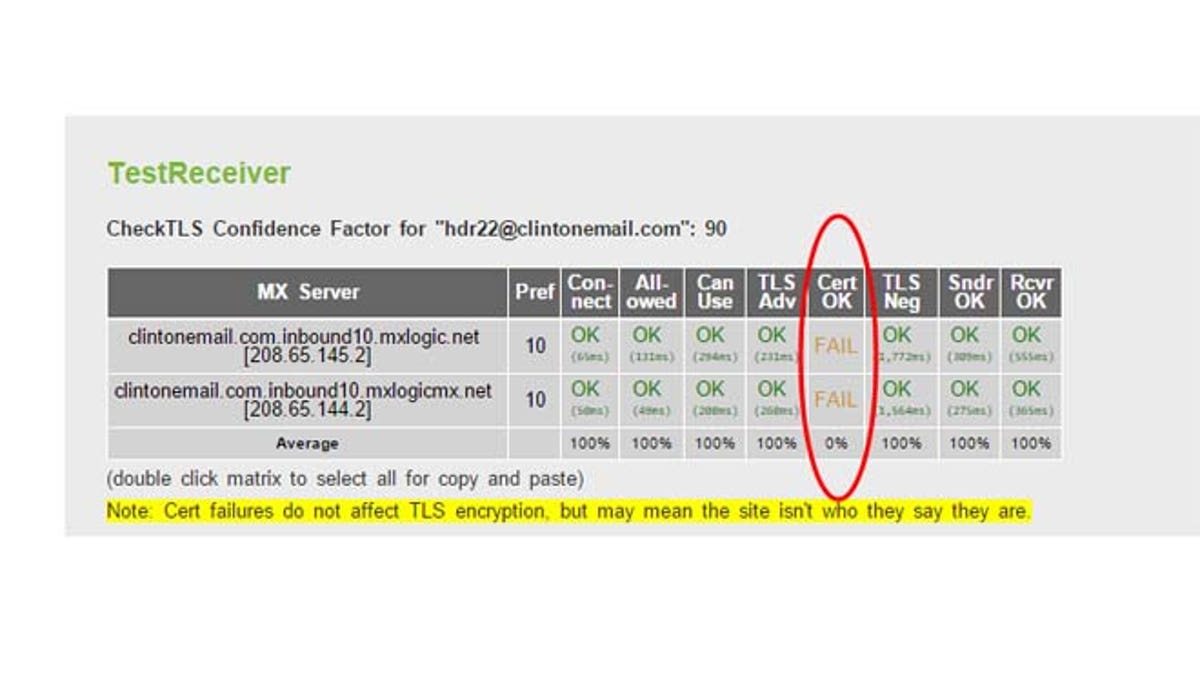
Work on the “replica” of the Clinton system also determined that the certificate for its TLS, or Transport Layer Security, is invalid – a lapse that “makes the site less secure,” the source said. A screen-grab provided to Fox News and shown here, illustrating the results of this test, showed the word “FAIL” appearing twice in a multifaceted stress-test for the security defenses of clintonemail.com.
Perhaps most concerning, private analysts determined that clintonemail.com has been running an older model of Microsoft Internet Information Services, or IIS – specifically version 7.5, which has been documented to leave users exposed on multiple fronts. The website CVEDetails.com, which bills itself as “the ultimate security vulnerability datasource,” is awash with descriptions of serious security vulnerabilities associated with version 7.5, including “memory corruption,” “password disclosure vulnerability,” and the enabling of “remote attackers to execute arbitrary code or cause a denial of service.”
The cyberlab technician who discovered the Clintons’ use of version 7.5 marveled at “the vulnerabilities the Clintons are ignoring” in an email to Fox News. “This is a big deal and just the thing real-world hackers look for in a target and will exploit to the max,” the source said.
“Several of these vulnerabilities have been known since 2010 and yet HRC is running official State comms through it.”
Coupled with the earlier disclosure, first reported by Bloomberg, that the Clinton system used a commercial encryption product with “a default encryption certificate, instead of one purchased specifically for Ms. Clinton’s service,” these latest revelations suggest a complacent approach to server security on the part of the secretary and her aides.
Representatives for Clinton have not responded to multiple requests for comment. Spokesman Nick Merrill has released a FAQ document stating that “robust protections were put in place” on the server, with “upgrades and techniques employed over time as they became available, including consulting and employing third party experts.” Merrill added that “there is no evidence” that the server was ever hacked, and said there was never an unauthorized intrusion into the secretary’s email.
The Merrill document stated that Clinton’s server “was physically located on her property, which is protected by U.S. Secret Service,” but did not address its present location.
Bruce F. Webster, an IT expert with 40 years of corporate experience -- the last 15 spent testifying on IT issues in civil litigation -- raised the question of whether Clinton's server has been moved at some point. On his blog, "And Still I Persist," Webster entitled his latest post "No, we still don't know where the Clinton server is, was, has been." In an email to Fox News, Webster referenced suggestions that the server remains in Chappaqua, where it was first registered, and stated: "I consider that the least likely location at this point."
Just the original decision to use a private email account, with Clinton’s own surname embedded in it, has baffled the hacker community. The analyst with experience in the intelligence community, a “white hat” hacker -- the kind corporate firms retain to conduct “penetration testing” that exposes businesses’ cybersecurity lapses -- told Fox News: “If we learned that the foreign minister of a major foreign country was using her own private server to send and receive emails, and was relying on outdated commercial software to operate and protect it, that’d be a hallelujah moment for us.”













































